
Don’t get phished.
Train your people effectively against phishing attacks with Dragons of Deception. Our learning campaigns and continuous simulations help you build lasting safe behavior.
How it works
The new way of phishing training.
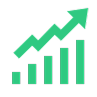
Dragons of Deception offers an energetic learning experience. A learning campaign like a TV series: short scans, learning bites, mini games, videos and tests, wrapped in seasons and episodes. Spread them out over 9 weeks or just binge them all.
Smart nudges keep everyone hooked, resulting in high participation.
Benefits
Limit risks with proven behaviour interventions.

A program that runs itself.

Employees who participate.

Results to be proud of.
Compliance check.
Our products
Make your organisation resillient to phishing.
Dragons of Deception
Phishing learning campaign
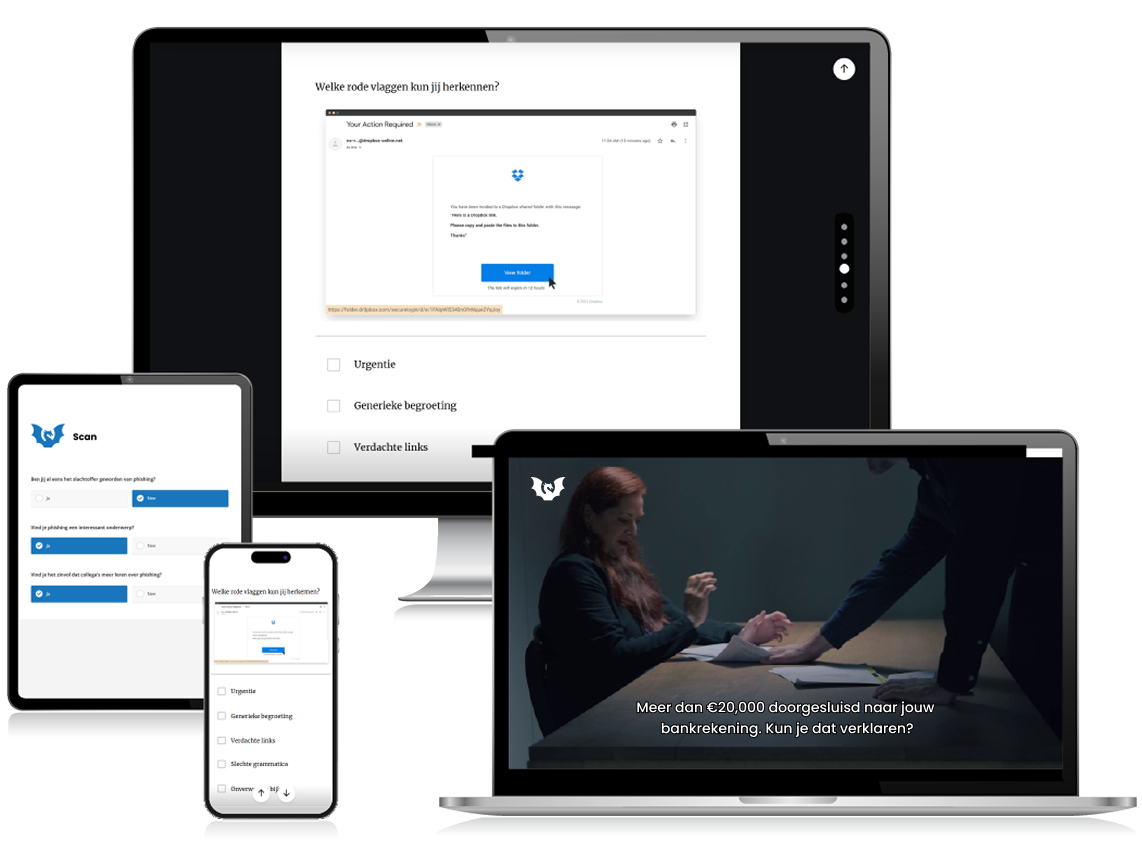
A learning campaign full of surprising and short learning interventions like mini games and videos. Smart nudges ensure high participation, while the process for managers is completely automated.
Continuous Phishing
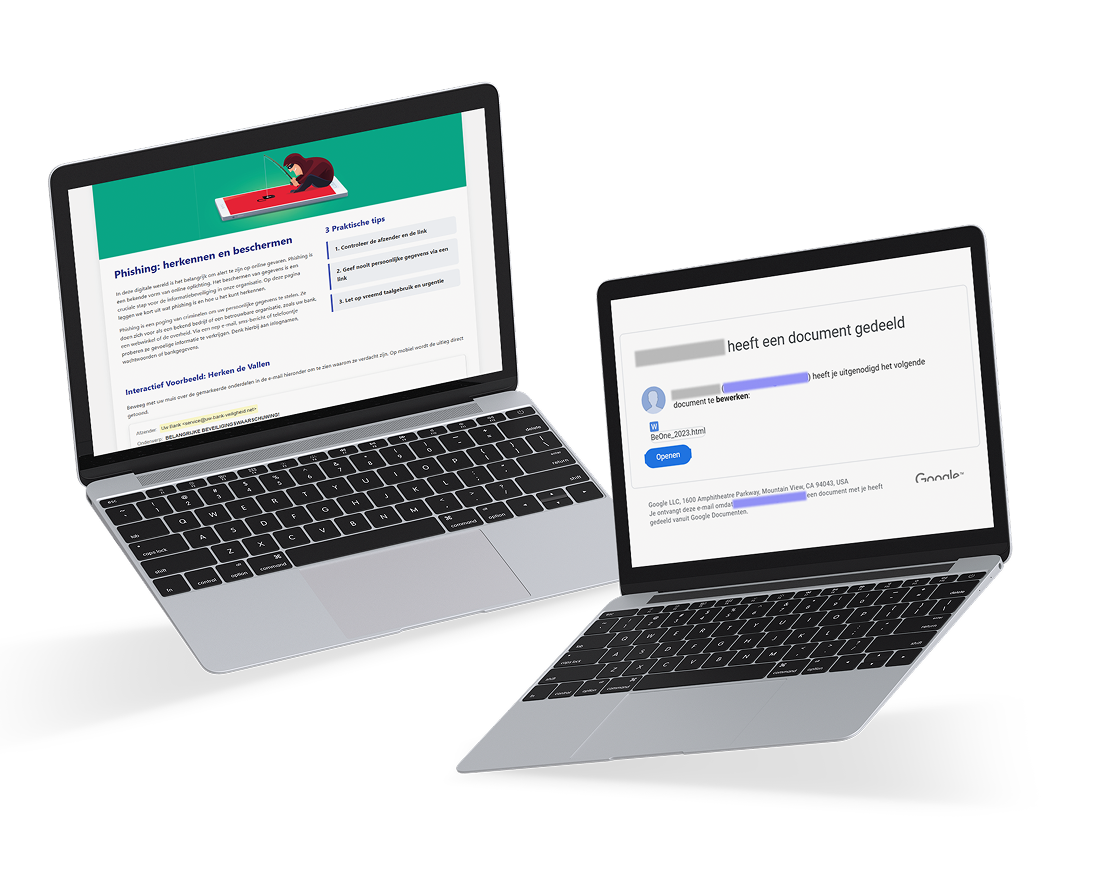
Phishing simulations
The combination
Phishing learning campaign & phishing simulation
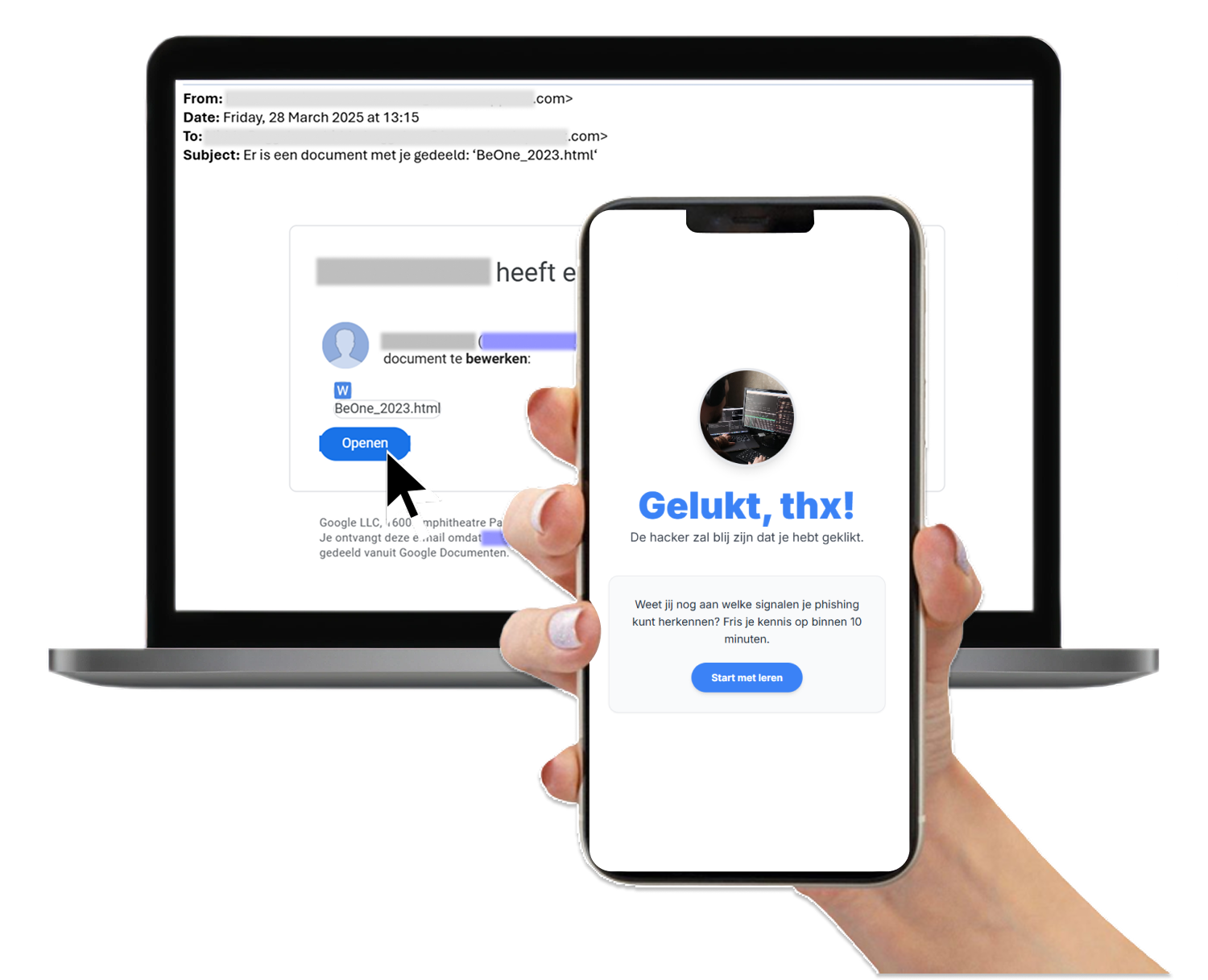
The phishing learning campaign raises awareness and alertness. The phishing simulations test behaviour. If someone clicks on a phishing e-mail from the simulation, an extra learning bite automatically follows. This way the learning campaign continues as normal, but is supplemented based on real behaviour.
What your people will learn.
01
Psychology of the hacker
Understand why hackers use phishing and what persuasion techniques they employ.
02
Recognise and report
Develop a sharp eye for suspicious links, senders and requests, and learn how to act.
03
Specific threats
Distinguish different types of phishing from genuine communication.
Brochure
Everything in one overview.

Want to know more?
I would be happy to discuss how you can use Dragons of Deception in your organisation.
Plan a 30-minute online meeting below.
Tim Welling

